Network Security
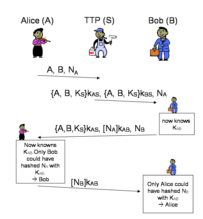
We are actively working on security protocols and methods for authentication as well as access control. To evaluate security properties, we also apply formal methods like model checking. We work with new protocols or modifications of existing protocols that use hardware security chips as the Trusted Platform Module (TPM) or Smart Cards.
Protection against DoS Attacks
Today (Distributed) Denial of Service Attacks are a major threat to the internet. In the past years there were attacks against the Internet infrastructure (i.e. DNS root servers), various services and companies and even against private persons using specific services (i.e. XBOX live). We are researching different ways to mitigate this threat.
Some networks are specially vulnerable against DoS attacks, for example if a core service that other services depend on has only limited capacity available. An attack against such a service will also affect dependend services. We are working on methods to check network and service topologies for such weaknesses.
Defense against ongoing attacks is easier if the defender has the possibility to flexibly re-configure his network topology. We are working on virtualization techniques that allow to change the network on the fly to limit the consequences on an attack.
Another research topic is the defense of HTTP-Servers by redirecting traffic between the client and multiple proxies. This way the attacker has to spend more resources to cause load on the server.
Honeypots, Malware Analysis and Intrusion Detection
In order to protect networks against Distributed Denial of Service Attacks understanding the mechanisms which are used to conduct these attacks is crucial.
Our research activities therefore deal with the investigation of malware and botnets. We employ different kinds of honeypots in order to collect worms and other kinds of malware. All collected malware is automatically analyzed in sandbox environments in order to gain knowledge about its functionality and the botnets which are build with it. Using the results of our analysis enables us to enhance our traffic analysis and intrusion detection methods.
Network Access Control and Applications of Trusted Computing Technology
We work on authentication and authorization in various areas of networking. Peer-to-Peer networks and other self-organising systems, Web Services, and sensor networks are some examples. Especially in the context of (partially) self-organising systems, we investigate solutions that go beyond classic X.509 PKI or shared key infrastructures.
To this end, we develop cryptographic protocols, especially for authentication and conduct security analyses. One way to do this is to apply methods of model checking. We also adapt yet unprotected applications and services to be able to use standardized state-of-the-art security solutions (TLS, IPSec, WS Security, XACML, …) with them.
We also work on security solutions that use the Trusted Platform Module (TPM) technology. One use-case for TPM is the secure storage of keys. Users cannot interfere and copy keys to insecure locations. The same is true for attackers who might want to get hold of the key to attack the network and its services. We also investigate Remote Attestation with the help of TPM. Remote Attestation allows to signal to another party that only a certain set of applications and a certain version of an Operating System (OS) is running on a computer. The primary usage is to avoid that worms, trojan horses or users of the system comprise its security by installing attack software. This is especially useful in business settings where even priviledged users could be attackers that need to be stopped.
Scientists: Michael Oberrauch, Dr. Holger Kinkelin, Dr. Johann Schlamp, Christian Dietze, M.Sc., Prof. Dr.-Ing. Georg Carle, Markus Sosnowski, M.Sc., Stefan Genchev, M. Sc., Prof. Dr. Marc-Oliver Pahl, Dr. Lars Wüstrich, Lion Steger, Prof. Dr. Ralph Holz, Veronika Bauer, Marcel Kempf, M.Sc., Tim Betzer, Filip Rezabek
Projects: ACE-SUPPRA, Cybersecurity Polygon Program, VITAF, AutoMon, DecADe, X-Check, SENDATE, securemail, SafeCloud, BaaS, SURF, IDEM, SpoVNet, Peeroskop, AutHoNe, ResumeNet, SASER, EINS, SecFuNet, ANSII
Publications
| 2024-03-01 | Filip Rezabek*, Marcin Bosk*, Leander Seidlitz, Jörg Ott, Georg Carle, “Context Matters: Lessons Learned from Emulated and Simulated TSN Environments,” in 3rd International Workshop on Negative Results in Pervasive Computing (PerFail 2024), Biarritz, France, Mar. 2024. [Pdf] [Bib] |
| 2024-01-01 | Burak Öz, Jonas Gebele, Parshant Singh, Filip Rezabek, Florian Matthes, “Playing the MEV Game on a First-Come-First-Served Blockchain,” Jan. 2024. [Preprint] [Bib] |
| 2023-11-01 | Burak Öz, Filip Rezabek, Jonas Gebele, Felix Hoops, Florian Matthes, “A Study of MEV Extraction Techniques on a First-Come-First-Served Blockchain,” Nov. 2023. [Preprint] [Bib] |
| 2023-06-01 | Marcin Bosk*, Filip Rezabek*, Johannes Abel, Kilian Holzinger, Max Helm, Georg Carle, Jörg Ott, “Simulation and Practice: A Hybrid Experimentation Platform for TSN,” in 22nd International Federation for Information Processing (IFIP) Networking Conference, Barcelona, Spain, Jun. 2023. [Bib] |
| 2023-03-01 | Filip Rezabek*, Marcin Bosk*, Georg Carle, Jörg Ott, “TSN Experiments Using COTS Hardware and Open-Source Solutions: Lessons Learned,” in 2nd International Workshop on Negative Results in Pervasive Computing (PerFail 2023), Atlanta, USA, Mar. 2023. Best Paper Award [Pdf] [Slides] [Bib] |
| 2023-01-01 | Marco Hoffmann, Gerald Kunzmann, Torsten Dudda, Ralf Irmer, Admela Jukan, Gordana Macher, Abdullah Ahmad, Florian R. Beenen, Arne Bröring, Felix Fellhauer, Gerhard Fettweis, Frank H. P. Fitzek, Norman Franchi, Florian Gast, Bernd Haberland, Sandra Hoppe, Sadaf Joodaki, Nandish P. Kuruvatti, Chu Li, Miguel Lopez, Fidan Mehmeti, Thomas Meyerhoff, Lorenzo Miretti, Giang T. Nguyen, Mohammad Parvini, Rastin Pries, Rafael F. Schaefer, Peter Schneider, Dominic Schupke, Stephanie Strassner, Henning Stubbe, Andra M. Voicu, “A secure and resilient 6G architecture vision of the German flagship project 6G-ANNA,” IEEE Access, 2023. [Pdf] [DOI] [Bib] |
| 2023-01-01 | Christian Lübben, Marc-Oliver Pahl, “Distributed Device-Specific Anomaly Detection for Resource-Constrained Devices,” in NOMS 2023-2023 IEEE/IFIP Network Operations and Management Symposium, 2023, pp. 1–3. Best Demo Award [Url] [DOI] [Bib] |
| 2023-01-01 | Christian Lübben, Marc-Oliver Pahl, “Distributed Device-Specific Anomaly Detection using Deep Feed-Forward Neural Networks,” in NOMS 2023-2023 IEEE/IFIP Network Operations and Management Symposium, 2023, pp. 1–9. [Url] [DOI] [Bib] |
| 2022-12-01 | Richard von Seck, Filip Rezabek, Benedikt Jaeger, Sebastian Gallenmüller, Georg Carle, “BFT-Blocks: The Case for Analyzing Networking in Byzantine Fault Tolerant Consensus,” in 2022 IEEE 21st International Symposium on Network Computing and Applications (NCA), Dec. 2022, vol. 21, pp. 35–44. [DOI] [Bib] |
| 2022-11-01 | Filip Rezabek, Max Helm, Tizian Leonhardt, Georg Carle, “PTP Security Measures and their Impact on Synchronization Accuracy,” in 18th International Conference on Network and Service Management (CNSM 2022), Thessaloniki, Greece, Nov. 2022. [Pdf] [Bib] |
| 2021-05-01 | Lars Wüstrich, Lukas Schröder, Marc-Oliver Pahl, “Cyber-Physical Anomaly Detection for ICS,” in 2021 IEEE/IFIP Symposium on Integrated Network and Service Management (IM 2021), Bordeaux, France (Virtual Conference), May 2021. [Bib] |
| 2021-01-01 | Christian Lübben, Marc-Oliver Pahl, “Advances in ML-Based Anomaly Detection for the IoT,” in 2021 5th Cyber Security in Networking Conference (CSNet), 2021, pp. 18–22. [Url] [DOI] [Bib] |
| 2020-06-01 | Maximilian Pudelko, Paul Emmerich, Sebastian Gallenmüller, Georg Carle, “Performance Analysis of VPN Gateways,” in IFIP Networking 2020, Paris, France, Jun. 2020. [Pdf] [Bib] |
| 2020-04-01 | Holger Kinkelin, Richard von Seck, Christoph Rudolf, Georg Carle, “Hardening X.509 Certificate Issuance using Distributed Ledger Technology,” in NOMS 2020 - IEEE/IFIP Workshop DISSECT 2020, Budapest, Hungary, Apr. 2020. [Preprint] [Bib] |
| 2019-05-01 | Benedikt Jaeger, Dominik Scholz, Daniel Raumer, Fabien Geyer, Georg Carle, “Reproducible Measurements of TCP BBR Congestion Control,” Computer Communications, vol. 144, pp. 31–43, May 2019. [Pdf] [DOI] [Bib] |
| 2019-04-01 | Holger Kinkelin, Heiko Niedermayer, Marc-Oliver Müller, Georg Carle, “Multi-party authorization and conflict mediation for decentralized configuration management processes,” in IM 2019 - IEEE/IFIP Workshop HotNSM 2019, Washington D.C., USA, Apr. 2019. [Preprint] [Bib] |
| 2019-04-01 | Cora Perner, Holger Kinkelin, Georg Carle, “Adaptive Network Management for Safety-Critical Systems,” in IM 2019 - IEEE/IFIP Workshop Dissect 2019, Washington D.C., USA, Apr. 2019. [Bib] |
| 2019-04-01 | Marc-Oliver Pahl, Lorenzo Donini, “Giving IoT Edge Services an Identity and Changeable Attributes,” in International Symposium on Integrated Network Management (IM), Washington DC, USA, Apr. 2019. [Pdf] [Bib] |
| 2019-03-01 | Wouter B. de Vries, Quirin Scheitle, Moritz Müller, Willem Toorop, Ralph Dolmans, Roland van Rijswijk-Deij, “A First Look at QNAME Minimization in the Domain Name System,” in Proceedings of the Passive and Active Measurement Conference (PAM 2019), Best Dataset Award, Puerto Varas, Chile, Mar. 2019. [Url] [Bib] |
| 2018-12-01 | Cornelius Diekmann, Johannes Naab, Andreas Korsten, Georg Carle, “Agile Network Access Control in the Container Age,” IEEE Transactions on Network and Service Management, Dec. 2018. [Pdf] [DOI] [Bib] |
| 2018-12-01 | Fabien Geyer, “DeepComNet: Performance Evaluation of Network Topologies using Graph-Based Deep Learning,” Performance Evaluation, Dec. 2018. [Pdf] [DOI] [Bib] |
| 2018-11-01 | Quirin Scheitle, Oliver Hohlfeld, Julien Gamba, Jonas Jelten, Torsten Zimmermann, Stephen D. Strowes, Narseo Vallina-Rodriguez, “A Long Way to the Top: Significance, Structure, and Stability of Internet Top Lists,” in Internet Measurement Conference (IMC’18), IMC’18 Community Contribution Award, Boston, USA, Nov. 2018, pp. 478–493. [Homepage] [Rawdata] [Arxiv] [DOI] [Bib] |
| 2018-11-01 | Quirin Scheitle, Oliver Gasser, Theodor Nolte, Johanna Amann, Lexi Brent, Georg Carle, Ralph Holz, Thomas C. Schmidt, Matthias Wählisch, “The Rise of Certificate Transparency and Its Implications on the Internet Ecosystem,” in Internet Measurement Conference (2018), Boston, USA, Nov. 2018, pp. 343–349. [Rawdata] [Arxiv] [DOI] [Bib] |
| 2018-11-01 | Oliver Gasser, Quirin Scheitle, Pawel Foremski, Qasim Lone, Maciej Korczynski, Stephen D. Strowes, Luuk Hendriks, Georg Carle, “Clusters in the Expanse: Understanding and Unbiasing IPv6 Hitlists,” in Proceedings of the 2018 Internet Measurement Conference, New York, NY, USA, Nov. 2018. [Pdf] [Slides] [Homepage] [Rawdata] [Arxiv] [Blog] [DOI] [Bib] |
| 2018-10-01 | Paul Emmerich, Maximilian Pudelko, Quirin Scheitle, Georg Carle, “Efficient Dynamic Flow Tracking for Packet Analyzers,” in CloudNet, Tokyo, Japan, Oct. 2018. [Pdf] [Bib] |
| 2018-09-01 | Dominik Scholz, Daniel Raumer, Paul Emmerich, Alexander Kurtz, Krzysztof Lesiak, Georg Carle, “Performance Implications of Packet Filtering with Linux eBPF,” in Teletraffic Congress (ITC 30), 2018 30th International, Vienna, Austria, Sep. 2018. [Pdf] [Slides] [Bib] |
| 2018-08-01 | Fabien Geyer, Georg Carle, “Learning and Generating Distributed Routing Protocols Using Graph-Based Deep Learning,” in Proceedings of the 2018 SIGCOMM Workshop on Big Data Analytics and Machine Learning for Data Communication Networks, Budapest, Hungary, Aug. 2018, pp. 40–45. [Pdf] [DOI] [Bib] |
| 2018-05-01 | Dominik Scholz, Benedikt Jaeger, Lukas Schwaighofer, Daniel Raumer, Fabien Geyer, Georg Carle, “Towards a Deeper Understanding of TCP BBR Congestion Control,” in IFIP Networking 2018, Zurich, Switzerland, May 2018. [Pdf] [Sourcecode] [DOI] [Bib] |
| 2018-04-01 | Quirin Scheitle, Taejoong Chung, Jens Hiller, Oliver Gasser, Johannes Naab, Roland van Rijswijk-Deij, Oliver Hohlfeld, Ralph Holz, Dave Choffnes, Alan Mislove, Georg Carle, “A First Look at Certification Authority Authorization (CAA),” ACM SIGCOMM Computer Communications Review (CCR), Apr. 2018. [Url] [Pdf] [Preprint] [Homepage] [Rawdata] [Bib] |
| 2018-04-01 | Holger Kinkelin, Valentin Hauner, Heiko Niedermayer, Georg Carle, “Trustworthy Configuration Management for Networked Devices using Distributed Ledgers,” in NOMS 2018 - IEEE/IFIP DOMINOS workshop, Apr. 2018. [Preprint] [Bib] |
| 2018-03-01 | Quirin Scheitle, Jonas Jelten, Oliver Hohlfeld, Luca Ciprian, Georg Carle, “Structure and Stability of Internet Top Lists,” in PAM’18 Poster, Berlin, Mar. 2018. [Arxiv] [Bib] |
| 2018-03-01 | Oliver Gasser, Benjamin Hof, Max Helm, Maciej Korczynski, Ralph Holz, Georg Carle, “In Log We Trust: Revealing Poor Security Practices with Certificate Transparency Logs and Internet Measurements,” in Proceedings of the Passive and Active Measurement Conference (PAM 2018), Best Paper Award, Berlin, Germany, Mar. 2018. [Url] [Pdf] [Slides] [Sourcecode] [Rawdata] [Blog] [Bib] |
| 2018-03-01 | Tobias Brunnwieser, Oliver Gasser, Sree Harsha Totakura, Georg Carle, “Live Detection and Analysis of HTTPS Interceptions,” in Passive and Active Measurement Conference (PAM), Poster, Berlin, Germany, Mar. 2018. [Pdf] [Poster] [Bib] |
| 2018-02-01 | F. Helfert, H. Niedermayer, G. Carle, “Evaluation of Algorithms for Multipath Route Selection over the Internet ,” in 14th International Workshop on Design of Reliable Communication Networks (DRCN), Feb. 2018. [Pdf] [Bib] |
| 2017-12-01 | Fabien Geyer, “Performance Evaluation of Network Topologies using Graph-Based Deep Learning,” in Proc. 11th EAI International Conference on Performance Evaluation Methodologies and Tools, Venice, Italy, Dec. 2017. [Pdf] [DOI] [Bib] |
| 2017-11-01 | Johanna Amann*, Oliver Gasser*, Quirin Scheitle*, Lexi Brent, Georg Carle, Ralph Holz, “Mission Accomplished? HTTPS Security after DigiNotar,” in Proceedings of the Internet Measurement Conference (IMC 2017), IMC’17 Community Contribution Award, IRTF Applied Networking Research Prize (ANRP) 2018, London, UK, Nov. 2017. [Url] [Pdf] [Slides] [Sourcecode] [Rawdata] [Bib] |
| 2017-10-01 | Oliver Gasser, Quirin Scheitle, Benedikt Rudolph, Carl Denis, Nadja Schricker, Georg Carle, “The Amplification Threat Posed by Publicly Reachable BACnet Devices,” Journal of Cyber Security and Mobility, Oct. 2017. [Url] [Pdf] [Bib] |
| 2017-08-01 | Quirin Scheitle, Matthias Wählisch, Oliver Gasser, Thomas C. Schmidt, Georg Carle, “Towards an Ecosystem for Reproducible Research in Computer Networking,” in ACM SIGCOMM Reproducibility Workshop, Los Angeles, USA, Aug. 2017. [Pdf] [Slides] [Bib] |
| 2017-07-01 | Paul Emmerich, Daniel Raumer, Sebastian Gallenmüller, Florian Wohlfart, Georg Carle, “Throughput and Latency of Virtual Switching with Open vSwitch: A Quantitative Analysis,” Journal of Network and Systems Management, Jul. 2017. [Pdf] [DOI] [Bib] |
| 2017-06-01 | Paul Emmerich, Maximilian Pudelko, Sebastian Gallenmüller, Georg Carle, “FlowScope: Efficient Packet Capture and Storage in 100 Gbit/s Networks,” in IFIP Networking 2017, Stockholm, Sweden, Jun. 2017. [Pdf] [Bib] |
| 2017-06-01 | Quirin Scheitle, Oliver Gasser, Patrick Sattler, Georg Carle, “HLOC: Hints-Based Geolocation Leveraging Multiple Measurement Frameworks,” in Network Traffic Measurement and Analysis Conference (TMA), Best Dataset Award, Dublin, Ireland, Jun. 2017. [Pdf] [Slides] [Rawdata] [Arxiv] [Bib] |
| 2017-06-01 | Quirin Scheitle, Oliver Gasser, Minoo Rouhi, Georg Carle, “Large-Scale Classification of IPv6-IPv4 Siblings with Variable Clock Skew,” in Network Traffic Measurement and Analysis Conference (TMA), Jun. 2017. [Pdf] [Slides] [Rawdata] [Recording] [Arxiv] [Bib] |
| 2017-06-01 | Matthias Wachs, Quirin Scheitle, Georg Carle, “Push Away Your Privacy: Precise User Tracking Based on TLS Client Certificate Authentication,” in Network Traffic Measurement and Analysis Conference (TMA), Best Paper Award TMA’17, IEEE ComSoc ITC Best Paper Award 2017, Jun. 2017. [Pdf] [Slides] [Recording] [Bib] |
| 2017-06-01 | Marcel von Maltitz, Cornelius Diekmann, Georg Carle, “Privacy Assessment using Static Taint Analysis (Tool Paper),” in FORTE – 37th IFIP International Conference on Formal Techniques for Distributed Objects, Components and Systems, Neuchatel, Switzerland, Jun. 2017. [Url] [Preprint] [Slides] [Sourcecode] [Rawdata] [Extended version] [DOI] [Bib] |
| 2017-05-01 | Oliver Gasser, Quirin Scheitle, Carl Denis, Nadja Schricker, Georg Carle, “Security Implications of Publicly Reachable Building Automation Systems,” in Proc. 2nd Int. Workshop on Traffic Measurements for Cybersecurity, San Jose, CA, USA, May 2017. [Pdf] [Bib] |
| 2017-02-01 | Oliver Gasser, Quirin Scheitle, Carl Denis, Nadja Schricker, Georg Carle, “Öffentlich erreichbare Gebäudeautomatisierung: Amplification-Anfälligkeit von BACnet und Deployment-Analyse im Internet und DFN,” in 24. DFN-Konferenz Sicherheit in vernetzten Systemen, Hamburg, Germany, Feb. 2017. [Pdf] [Bib] |
| 2016-11-01 | Marcel von Maltitz, Cornelius Diekmann, Georg Carle, “Taint Analysis for System-Wide Privacy Audits: A Framework and Real-World Case Studies.” 1st Workshop for Formal Methods on Privacy, Nov-2016. workshop without proceedings [Preprint] [Sourcecode] [Rawdata] [Bib] |
| 2016-10-01 | Julius Michaelis, Cornelius Diekmann, “LOFT – Verified Migration of Linux Firewalls to SDN,” Archive of Formal Proofs, Oct. 2016. Formal proof development [Url] [Bib] |
| 2016-10-01 | Daniel Raumer, Sebastian Gallenmüller, Paul Emmerich, Lukas Märdian, Florian Wohlfart, Georg Carle, “Efficient Serving of VPN Endpoints on COTS Server Hardware,” in 2016 IEEE 5th tnternational Conference on Cloud Networking (CloudNet’16), Pisa, Italy, Oct. 2016. [Pdf] [Bib] |
| 2016-09-01 | Cornelius Diekmann, Lars Hupel, “Iptables_Semantics,” Archive of Formal Proofs, Sep. 2016. Formal proof development [Url] [Bib] |
| 2016-09-01 | Daniel Sel, Sree Harsha Totakura, Georg Carle, “sKnock: Scalable Port-Knocking for Masses ,” in Workshop on Mobility and Cloud Security & Privacy, Budapest, Hungary, Sep. 2016. [Preprint] [Sourcecode] [Bib] |
| 2016-08-01 | Julius Michaelis, Cornelius Diekmann, “Routing,” Archive of Formal Proofs, Aug. 2016. Formal proof development [Url] [Bib] |
| 2016-08-01 | Cornelius Diekmann, Julius Michaelis, Max Haslbeck, “Simple Firewall,” Archive of Formal Proofs, Aug. 2016. Formal proof development [Url] [Bib] |
| 2016-06-01 | Cornelius Diekmann, Julius Michaelis, Lars Hupel, “IP Addresses,” Archive of Formal Proofs, Jun. 2016. Formal proof development [Url] [Bib] |
| 2016-06-01 | Johann Schlamp, Ralph Holz, Quentin Jacquemart, Georg Carle, Ernst Biersack, “HEAP: Reliable Assessment of BGP Hijacking Attacks,” IEEE Journal on Selected Areas in Communications, Special Issue on Measuring and Troubleshooting the Internet: Algorithms, Tools and Applications; Volume 34 #6; ISSN: 0733-8716, pp. 1849–1861, Jun. 2016. [Bib] |
| 2016-05-02 | Matthias Wachs, Nadine Herold, Stephan-A. Posselt, Florian Dold, Georg Carle, “GPLMT: A Lightweight Experimentation and Testbed Management Framework,” in Passive and Active Measurement: 17th International Conference, PAM 2016, Heraklion, Greece, Mar. 2016. [Url] [Pdf] [DOI] [Bib] |
| 2016-05-01 | Cornelius Diekmann, Julius Michaelis, Maximilian Haslbeck, Georg Carle, “Verified iptables Firewall Analysis,” in IFIP Networking 2016, Vienna, Austria, May 2016. [Url] [Pdf] [Slides] [Sourcecode] [Rawdata] [Bib] |
| 2016-04-01 | Oliver Gasser, Felix Emmert, Georg Carle, “Digging for Dark IPMI Devices: Advancing BMC Detection and Evaluating Operational Security,” in Proc. 8th Int. Workshop on Traffic Monitoring and Analysis, Louvain-la-Neuve, Belgium, Apr. 2016. [Pdf] [Bib] |
| 2016-04-01 | N. Herold, S. Posselt, O. Hanka, G. Carle, “Anomaly Detection for SOME/IP using Complex Event Processing,” in 2ND IEEE/IFIP Workshop on Security for Emerging Distributed Network Technologies (DISSECT), Apr. 2016. [Bib] |
| 2016-01-01 | Nadine Herold, Matthias Wachs, Stephan-A. Posselt, Georg Carle, “An Optimal Metric-Aware Response Selection Strategy for Intrusion Response Systems,” in Foundations and Practice of Security: 8th International Symposium, FPS 2016, Quebec, Canada, October 24-26, 2016, Springer International Publishing, 2016. [Bib] |
| 2016-01-01 | Nadine Herold, Holger Kinkelin, Georg Carle, “Collaborative Incident Handling Based on the Blackboard-Pattern,” in Proceedings of the 3rd ACM Workshop on Information Sharing and Collaborative Security, New York, NY, USA, 2016. [Bib] |
| 2015-11-01 | Cornelius Diekmann, Lukas Schwaighofer, Georg Carle, “Certifying Spoofing-Protection of Firewalls,” in 11th International Conference on Network and Service Management, CNSM, Barcelona, Spain, Nov. 2015. [Url] [Preprint] [Sourcecode] [Rawdata] [DOI] [Bib] |
| 2015-11-01 | Cornelius Diekmann, Andreas Korsten, Georg Carle, “Demonstrating topoS: Theorem-Prover-Based Synthesis of Secure Network Configurations,” in 2nd International Workshop on Management of SDN and NFV Systems, manSDN/NFV, Barcelona, Spain, Nov. 2015. [Url] [Preprint] [Slides] [Sourcecode] [DOI] [Bib] |
| 2015-10-01 | Paul Emmerich, Sebastian Gallenmüller, Daniel Raumer, Florian Wohlfart, Georg Carle, “MoonGen: A Scriptable High-Speed Packet Generator,” in Internet Measurement Conference (IMC) 2015, IRTF Applied Networking Research Prize 2017, Tokyo, Japan, Oct. 2015. [Pdf] [Bib] |
| 2015-06-01 | Cornelius Diekmann, Lars Hupel, Georg Carle, “Semantics-Preserving Simplification of Real-World Firewall Rule Sets,” in 20th International Symposium on Formal Methods, Jun. 2015, pp. 195–212. [Url] [Preprint] [Slides] [Sourcecode] [Rawdata] [DOI] [Bib] |
| 2015-05-01 | Sebastian Gallenmüller, Paul Emmerich, Florian Wohlfart, Daniel Raumer, Georg Carle, “Comparison of Frameworks for High-Performance Packet IO,” in ACM/IEEE Symposium on Architectures for Networking and Communications Systems (ANCS 2015), Oakland, CA, USA, May 2015. [Pdf] [Bib] |
| 2015-05-01 | Sebastian Gallenmüller, Paul Emmerich, Daniel Raumer, Georg Carle, “MoonGen: Software Packet Generation for 10 Gbit and Beyond,” in 12th USENIX Symposium on Networked Systems Design and Implementation (NSDI 15), Oakland, CA, USA, May 2015. [Pdf] [Poster] [Bib] |
| 2015-05-01 | Marc-Oliver Pahl, “Data-Centric Service-Oriented Management of Things,” in 14th IFIP/IEEE Symposium on Integrated Network and Service Management (IM 2015), Ottawa, Canada, May 2015. [Pdf] [Bib] |
| 2015-04-01 | Paul Emmerich, Daniel Raumer, Florian Wohlfart, Georg Carle, “Assessing Soft- and Hardware Bottlenecks in PC-based Packet Forwarding Systems,” in Fourteenth International Conference on Networks (ICN 2015), Best Paper Award, Barcelona, Spain, Apr. 2015. [Pdf] [Bib] |
| 2015-04-01 | Timm Böttger, Lothar Braun, Oliver Gasser, Felix von Eye, Helmut Reiser, Georg Carle, “DoS Amplification Attacks – Protocol-Agnostic Detection of Service Abuse in Amplifier Networks,” in Proc. 7th Int. Workshop on Traffic Monitoring and Analysis, Barcelona, Spain, Apr. 2015. [Pdf] [Bib] |
| 2015-04-01 | Johann Schlamp, Ralph Holz, Oliver Gasser, Andreas Korsten, Quentin Jacquemart, Georg Carle, Ernst W. Biersack, “Investigating the Nature of Routing Anomalies: Closing in on Subprefix Hijacking Attacks,” in Proc. 7th Int. Workshop on Traffic Monitoring and Analysis, Barcelona, Spain, Apr. 2015. [Pdf] [Bib] |
| 2015-03-01 | Alexander Beifuß, Daniel Raumer, Paul Emmerich, Torsten M. Runge, Florian Wohlfart, Bernd E. Wolfinger, Georg Carle, “A Study of Networking Software Induced Latency,” in 2nd International Conference on Networked Systems 2015 (NetSys’15), Cottbus, Germany, Mar. 2015. [Pdf] [Bib] |
| 2015-02-01 | Felix von Eye, Timm Böttger, Helmut Reiser, Lothar Braun, Oliver Gasser, Georg Carle, “Detektion und Prävention von Denial-of-Service Amplification Attacken – Schutz des Netzes aus Sicht eines Amplifiers,” in Sicherheit in vernetzten Systemen: 22. DFN-Konferenz, Norderstedt, Deutschland, Feb. 2015, 1. Aufl., pp. H-1–H-13. [Bib] |
| 2014-12-01 | Paul Emmerich, Daniel Raumer, Florian Wohlfart, Georg Carle, “A Study of Network Stack Latency for Game Servers,” in 13th Annual Workshop on Network and Systems Support for Games (NetGames’14), Nagoya, Japan, Dec. 2014. [Pdf] [Bib] |
| 2014-10-01 | Paul Emmerich, Daniel Raumer, Florian Wohlfart, Georg Carle, “Performance Characteristics of Virtual Switching,” in 2014 IEEE 3rd International Conference on Cloud Networking (CloudNet’14), Luxembourg, Oct. 2014. [Pdf] [Bib] |
| 2014-10-01 | Holger Kinkelin, Marcel von Maltitz, Benedikt Peter, Cornelia Kappler, Heiko Niedermayer, Georg Carle, “Privacy Preserving Energy Management,” in Proceeding of City Labs Workshop in conjunction with the International Conference on Social Informatics (SocInfo 2014), Barcelona, Spain, Oct. 2014. [Pdf] [Bib] |
| 2014-09-01 | Diego Kreutz, Eduardo Feitosa, Hugo Cunha, Heiko Niedermayer, Holger Kinkelin, “Increasing the Resilience and Trustworthiness of OpenID Identity Providers for Future Networks and Services,” in Ninth International Conference on Availability, Reliability and Security (ARES), Sep. 2014, pp. 317–324. [Bib] |
| 2014-06-01 | Cornelius Diekmann, Stephan-A. Posselt, Heiko Niedermayer, Holger Kinkelin, Oliver Hanka, Georg Carle, “Verifying Security Policies using Host Attributes,” in FORTE – 34th IFIP International Conference on Formal Techniques for Distributed Objects, Components and Systems, Berlin, Germany, Jun. 2014, vol. 8461, pp. 133–148. [Pdf] [Preprint] [Slides] [Sourcecode] [Rawdata] [DOI] [Bib] |
| 2014-05-01 | Cornelius Diekmann, Lars Hupel, Georg Carle, “Directed Security Policies: A Stateful Network Implementation,” in Engineering Safety and Security Systems, Singapore, May 2014, vol. 150, pp. 20–34. [Url] [Pdf] [Preprint] [Slides] [Sourcecode] [DOI] [Bib] |
| 2014-05-01 | Oliver Gasser, Ralph Holz, Georg Carle, “A deeper understanding of SSH: results from Internet-wide scans,” in Proc. 14th Network Operations and Management Symposium (NOMS), Krakow, Poland, May 2014. [Pdf] [Bib] |
| 2014-02-01 | Holger Kinkelin, Michael Dorner, Georg Carle, “Lokale Integritätsverifikation von Systemen durch Java Smart Cards,” in Tagungsband des 24. SmartCard Workshop, Darmstadt, Germany, Feb. 2014. [Bib] |
| 2013-10-01 | Marc-Oliver Pahl, Heiko Niedermayer, Holger Kinkelin, Georg Carle, “Enabling Sustainable Smart Neighborhoods,” in 3rd IFIP Conference on Sustainable Internet and ICT for Sustainability 2013 (SustainIT 2013), Palermo, Italy, Oct. 2013. [Pdf] [Bib] |
| 2013-09-01 | Marc-Oliver Pahl, Georg Carle, “Taking Smart Space Users Into the Development Loop,” in UbiComp 2013 Adjunct (HomeSys 2013), Zürich, Switzerland, Sep. 2013. [Pdf] [Bib] |
| 2013-05-01 | Lothar Braun, Cornelius Diekmann, Nils Kammenhuber, Georg Carle, “Adaptive Load-Aware Sampling for Network Monitoring on Multicore Commodity Hardware,” in IFIP Networking 2013, New York, NY, May 2013. [Url] [Pdf] [Preprint] [Sourcecode] [Bib] |
| 2012-10-01 | Thomas Kothmayr, Corinna Schmitt, Wen Hu, Michael Bruenig, Georg Carle, “A DTLS Based End-To-End Security Architecture for the Internet of Things with Two-Way Authentication,” in Seventh IEEE International Workshop on Practical Issues in Building Sensor Network Applications (SenseApp), Clearwater (FL), USA, Oct. 2012. [Bib] |
| 2011-11-01 | Thomas Kothmayr, Wen Hu, Corinna Schmitt, Michael Brünig, Georg Carle, “Securing the Internet of Things with DTLS,” in Proceedings of the 9th ACM Conference on Embedded Networked Sensor Systems (SenSys), Poster Session, Seattle, USA, Nov. 2011. [Bib] |
| 2011-09-01 | Lothar Braun, Corinna Schmitt, Benoit Claise, Georg Carle, “Compressed IPFIX for smart meters in constrained networks.” Internet-Draft (work in progress), draft-braun-core-compressed-ipfix-03.txt, Sep-2011. [Url] [Bib] |
| 2010-09-01 | Alexander Klein, Lothar Braun, Corinna Schmitt, Georg Carle, “MAUS: A Multi-hop Autonomous Sensor Network for Monitoring Applications with Full IP-support,” in Proceedings of the 9. GI/ITG KuVS Fachgespräch Sensornetze (FGSN), Würzburg, Germany, Sep. 2010. [Bib] |
| 2010-08-01 | Holger Kinkelin, Andreas Müller, Georg Carle, “Security and Access control for future home networks.” Demo at IPTComm 2010, Munich, Germany, Aug-2010. [Bib] |
| 2010-08-01 | Marc-Oliver Pahl, Georg Carle, “Automatic control and Management Platform (ACMP).” Demo at IPTComm 2010, Munich, Germany, Aug-2010. [Url] [Bib] |
| 2010-06-01 | Holger Kinkelin, Heiko Niedermayer, Ralph Holz, Georg Carle, “TPM-based Access Control for the Future Internet (ext. abstract),” in 5th GI/ITG KuVS Workshop on Future Internet, Stuttgart, Germany, Jun. 2010. [Bib] |
| 2010-04-01 | Corinna Schmitt, Lothar Braun, Thomas Kothmayr, Georg Carle, “Collecting Sensor Data using Compressed IPFIX,” in Proceedings of the 9th ACM/IEEE International Conference on Information Processing in Sensor Networks (IPSN), Poster Session, Stockholm, Sweden, Apr. 2010. [Bib] |
| 2010-03-01 | Marc-Oliver Pahl, Andreas Müller, Mario Schuster, Thomas Luckenbach, Christoph Niedermeier, Juergen Reichmann, “AutHoNe - Autonomic Networking.” Celtic News, Mar-2010. [Bib] |
| 2010-02-01 | Thomas Kothmayr, Corinna Schmitt, Lothar Braun, Georg Carle, “Gathering Sensor Data in Home Networks with IPFIX,” in Proceedings of the 7th European Conference on Wireless Sensor Networks (EWSN 2010), Coimbra, Portugal, Feb. 2010. [Bib] |
| 2009-11-01 | Dirk Haage, Ralph Holz, “Optimization of Distributed Services with UNISONO (ext. abstract),” in GI/ITG KuVS Fachgespräch NGN Service Delivery Platforms & Service Overlay Networks, Berlin, Germany, Nov. 2009. [Bib] |
| 2009-11-01 | Ralph Holz, Dirk Haage, “CLIO/UNISONO: Practical Distributed and Overlay-Wide Network Measurement (ext. abstract),” in 4th GI/ITG KuVS Workshop on The Future Internet and 2nd Workshop on Economic Traffic Management (ETM), Zürich, Switzerland, Nov. 2009. [Bib] |
| 2009-10-01 | Corinna Schmitt, Lothar Braun, Georg Carle, “IPFIX for Wireless Sensors.” Internet-Draft (work in progress), draft-schmitt-6lowapp-ipfix-ws-00, Oct-2009. [Url] [Bib] |
| 2009-04-01 | Marc-Oliver Pahl Thomas Luckenbach Mario Schuster, “An Autonomic Home Networking Infrastructure,” ERCIM News - Special theme: Future Internet Technology, no. 77, p. 41, Apr. 2009. [Url] [Bib] |
| 2009-03-01 | Dirk Haage, Ralph Holz, Heiko Niedermayer, Pavel Laskov, “CLIO – A Cross-Layer Information Service for Overlay Network Optimization,” in Kommunikation in Verteilten Systemen (KiVS) 2009, Kassel, Germany, Mar. 2009. [Pdf] [Homepage] [Bib] |
| 2007-07-01 | Oliver Waldhorst, Roland Bless, Dirk Haage, et. al., “SpoVNet: An Architecture for Supporting Future Internet Applications,” in 7th Würzburg Workshop on IP: Joint EuroFGI and ITG Workshop on "Visions of Future Generation Networks", Würzburg, Germany, Jul. 2007. [Bib] |
Student Theses
| 2019-01-01 | Christian Kilb, “Privacy-preserving VoIP Signaling with Secure Multiparty Computation.” BA, 2019. Dr. Marcel von Maltitz, Richard von Seck [Pdf] [Bib] |
| 2017-01-01 | Sebastian Bruhn, “An Analysis of Linux Firewall Performance.” BA, 2017. Daniel Raumer, Lukas Schwaighofer, Johannes Naab [Pdf] [Bib] |
| 2016-09-01 | Benedikt Engeser, “Informed Route Selection Strategies for Multipath Routing.” MA, Sep-2016. Heiko Niedermayer, Sree Harsha Totakura [Pdf] [Bib] |
| 2016-07-01 | Julien Schmidt, “Active Probing and Deep Packet Inspection Detection Resistant Tunnelling Through HTTPS Connections.” BA, Jul-2016. Sree Harsha Totakura [Bib] |
| 2016-05-01 | Hugues Fafard, “Secure Port-Knocked Communications.” BA, May-2016. Sree Harsha Totakura [Pdf] [Bib] |
| 2016-03-01 | Daniel Sel, “Authenticated Scalable Port-Knocking.” BA, Mar-2016. Sree Harsha Totakura, Heiko Niedermayer [Pdf] [Bib] |
| 2016-01-01 | Stefan Smarzly, “Employment and Evaluation of Secure Multi-Party Computation for Privacy-Preserving Services in Smart Buildings.” MA, 2016. Marcel von Maltitz, Dr. Holger Kinkelin [Pdf] [Bib] |
| 2016-01-01 | Erkin Kirdan, “Traffic shaping and policing with DPDK.” GR, 2016. Paul Emmerich, Dominik Scholz, Daniel Raumer [Pdf] [Bib] |
| 2015-10-01 | Oliver R. Broome, “A Digital Wallet Implementation for Anonymous Cash.” BA, Oct-2015. Sree Harsha Totakura [Pdf] [Bib] |
| 2015-08-01 | Julius Bünger, “Implementation and Evaluation of Brahms in the GNUnet Framework.” BA, Aug-2015. Bartolomiej Polot, Sree Harsha Totakura [Pdf] [Bib] |
| 2015-06-01 | Markus Alexander Teich, “Group OTR and its Use-Cases.” IDP, Jun-2015. Sree Harsha Totakura [Bib] |
| 2015-01-01 | Daniel Hugenroth, “HRTP: A Broadcast-Based System for Unobservable Internet Telephony.” MA, 2015. Advisor: Lukas Schwaighofer, Supervisor: Prof. Georg Carle [Pdf] [Bib] |
